Kill Syscall
Understanding Unix Signals and Alarms
signal demo codeMotivation & Purpose
We created new processes using fork() system callWe delegated work to the newly created process using exec() system call
We passed messgaes and data using pipe() system call
How can you interrupt the processes?
For signaling /interrupting each other? kill() system call
In this lecture we will study kill() and signals in the next week
Examples for kill() syscall
- Consider g++ myProg.c You want to kill this process after you started the compilation..hit cntrl-C
- Consider execution of a program called “badprog” >badprog It core dumps .. What happened? The error in the program results in a signal to kernel to stop and dump the offending code
- Consider “kill –p
” Kill issues a termination signal to the process identified by the pid
Process Termination
- Normal completion, time limit exceeded, memory unavailable
- Bounds violation, protection error, arithmetic error, invalid instruction
- IO failure, Operator intervention, parent termination, parent request, killed by another process
- A number of other conditions are possible.
Segmentation fault : usually happens when you try write/read into/from a non-existent array/structure/object component. Or access a pointer to a dynamic data before creating it. (new etc.)
Bus error: Related to function call and return. You have messed up the stack where the return address or parameters are stored.
Unix Signals
Signals provide a simple method for transmitting software interrupts to UNIX process Signals cannot carry information directly, which limits their usefulness as an general inter-process communication mechanism However each type of signal is given a mnemonic name; Ex: SIGINT See signal.h for others SIGHUP, SIGINT, SIGILL, SIGTRAP, SIGFPE, SIGKILL SIGALRM (sent by kernel to a process after an alarm timer has expired) SIGTERM signal (signal id, function) simply arms the signal
Signal Value Action Comment
-------------------------------------------------------------------------
SIGHUP 1 Term Hangup detected on controlling terminal
or death of controlling process
SIGINT 2 Term Interrupt from keyboard
SIGQUI 3 Core Quit from keyboard
SIGILL 4 Core Illegal Instruction
SIGABR 6 Core Abort signal from abort(3)
SIGFP 8 Core Floating point exception
SIGKILL 9 Term Kill signal
SIGSEG 11 Core Invalid memory reference
SIGPIPE 13 Term Broken pipe: write to pipe with no readers
SIGALRM 14 Term Timer signal from alarm(2)
SIGTERM 15 Term Termination signal
SIGUSR1 30,10,16 Term User-defined signal 1
SIGUSR2 31,12,17 Term User-defined signal 2
SIGCHLD 20,17,18 Ign Child stopped or terminated
SIGCONT 19,18,25 Cont Continue if stopped
SIGSTOP 17,19,23 Stop Stop process
SIGTSTP 18,20,24 Stop Stop typed at tty
SIGTTIN 21,21,26 Stop tty input for background process
SIGTTOU 22,22,27 Stop tty output for background process
The signals SIGKILL and SIGSTOP cannot be caught, blocked, or ignored.
Realtime Signals
Linux supports real-time signals as originally defined in the POSIX.1b real-time extensions (and now included in POSIX.1-2001). Linux supports 32 real-time signals, numbered from 32 (SIGRTMIN) to 63 (SIGRT- MAX) Main difference is that these are queued and not lost. Realtime signals are delivered in guaranteed order.Intercept Signals
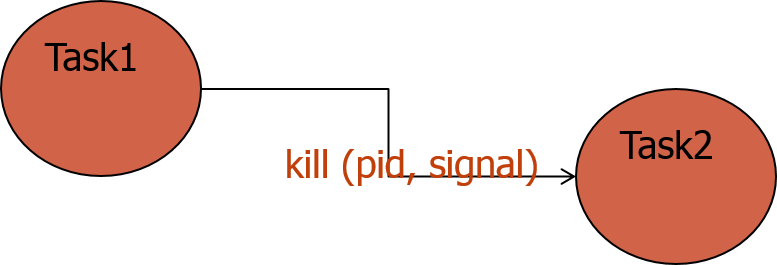
Two essentail parameters for kill() system call are (i) the destination process identifier (ii) and the signal code (reason for the intercept). kill(pid,signal#).
Signals are a useful way of handling intermittent data or rare error conditions.
Handling alarms & signals
Demo codeHandling alarms
- #include
- unsigned int alarm( unsigned int seconds );
- alarm(a); will start a timer for a secsonds and will interrupt the calling process after a secs.
- time(&t); will get you current time in the variable t declared as time_t t
- ctime(&t); will convert time to ascii format
- Alarm has a sigaction function that is set for configuring the alarm handler etc.
- sigaction(SIGALRM, &act, &oldact) ; the third paramter is for old action configuration
Illustrative Programs
- sigtest.c: Alarm set; alarm armed with a catcher; but program finishes before alarm.
- sigtest1.c: Alarm set; alarm armed with a catcher; program loop is interruped by alarm; control transferred to alarm catcher;
- sigHandler.c: Program sets a handler for signal 43 to be given from a keyboard; using kill(pid, 43)
- pingpong.c: two programs running keep interrupting each other with two different signals using kill(pid, #)
Things to observe in pingpong.c
- pause(): indefinite
- sleep(): sleep is random/finite time
- Programmatic use of kill() system call
- While loop
- Signal handlers
- Re-arming of the signals
Static and Volatile varaibles
Observe use of "static" modifier for a variable for count. That modifier turns a "automatic" (on the stack) variable into a globally accessible varaible.A variable should be declared volatile whenever its value could change unexpectedly. In practice, only three types of variables could change: Memory-mapped peripheral registers Global variables modified by an interrupt service routine Global variables within a multi-threaded application Registers in devices are abstracted for programmatic access as “volatile” type.
